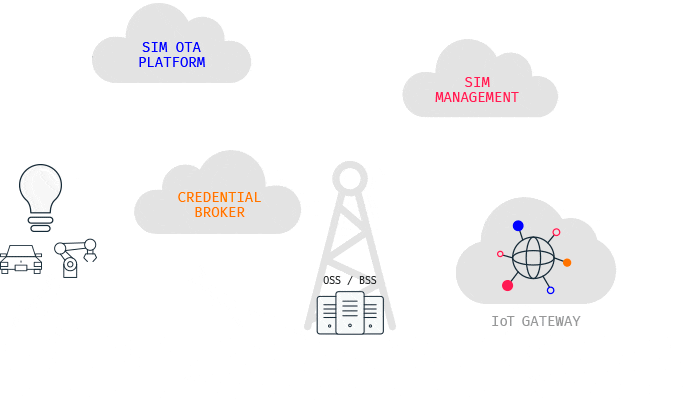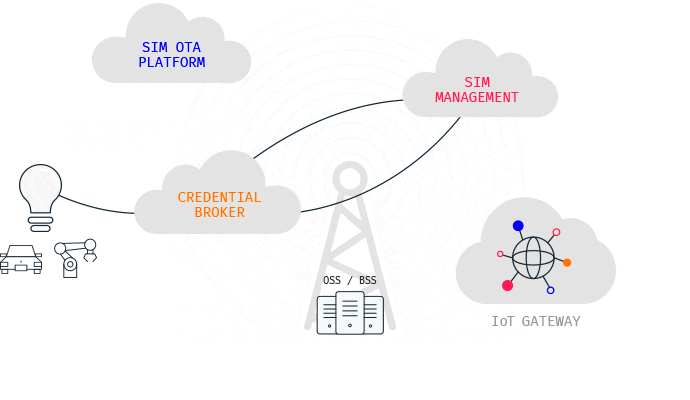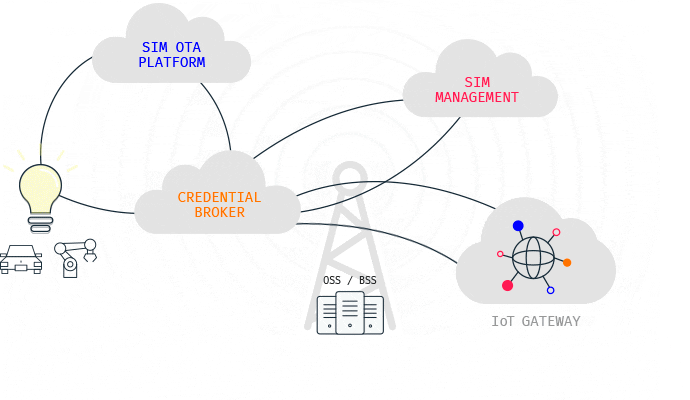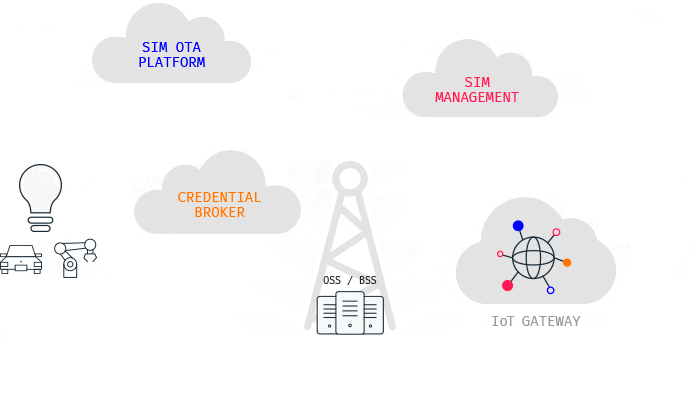
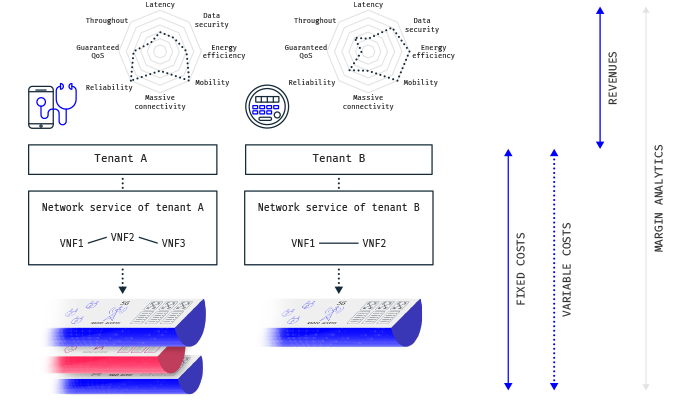
Roaming and Core Network
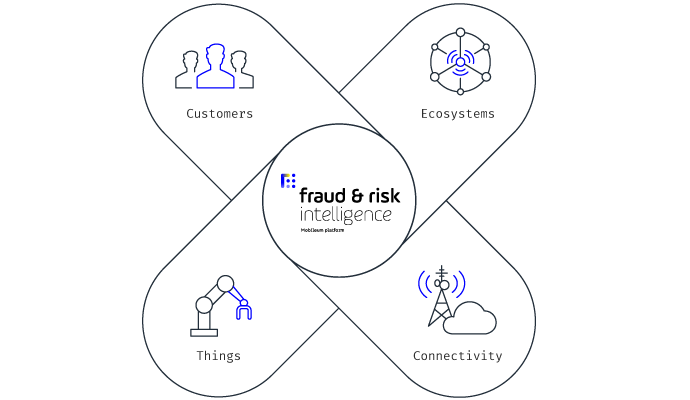
Risk Management
-
Revenue Assurance
- Usage Assurance
- Provisioning Assurance
- Rating & Billing Validation
- Prepaid Balance Validation
-
Fraud Management
- Revenue Share Fraud
- Bypass Fraud
- Roaming Fraud
- CLI Spoofing & Robocalling
- VoIP & SIP Fraud
- Dealers Fraud
- Subscription Fraud
- Data Fraud
- Telecom Wholesale Fraud
- SMS Bypass Fraud
Network Security
Testing and Monitoring
-
Domestic Network Testing
- SITE Platform
- 5G SA & NSA Performance Testing
- Core Network Testing
- Automation Framework
- RoboShark Automated PCAP Analysis
- Smartphone-based Testing
- Emergency Services Testing
- Video Performance Testing
- IoT & eSIM Performance Testing
- IMS and VoLTE Testing
- CS Voice, Data & Messaging Testing
- Mobile Money Testing
-
International Network Testing
- 5G Roaming Quality Assurance
- Roaming Quality Testing
- VoLTE Roaming Testing
- eSIM Macroscope
- Performance Intelligence
- Global IoT Connectivity Testing
- Roaming QoE at Large-Scale Events
5G
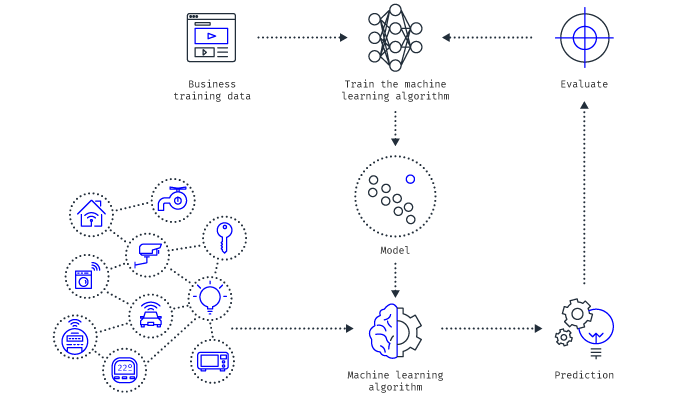
Internet of Things (IoT)
Service & Network Assurance
Check our Services
Check out our exclusive insightful content